Enable post-compromise data protection with MariaDB and Virgil Security’s PureKit
MariaDB deployments hold vast amounts of sensitive data such as intellectual property, state secrets, healthcare and financial records. HIPAA, GDPR and other government regulations require even more stringent protections and disclosures. Achieving post-compromise protection is seen as a necessary new tool available to DevOps teams.
At the first MariaDB Day in Brussels on February 2nd, Virgil Security’s CTO and co-founder Dmitry Dain presented a MariaDB demo based on the Virgil PureKit security framework that can protect stored passwords, PII and any other sensitive data even if the database had been breached – making it worthless to the attacker in the face of offline attacks (read more about security benefits in this blog post). Customers interested in the demo can find it in the PureKit MariaDB demo GitHub repository.
PureKit for MariaDB gives you:
- Record-level data encryption: Bring more targeted control to your database protection by encrypting separately down to the record level. With MariaDB’s existing data-at-rest encryption using transparent data encryption (TDE), data is encrypted by table or column, not record
- Per-user data encryption: Give end-users control over their own keys (including sharing privileges and role-based access) for ease of compliance with regulations like GDPR
- Post-compromise security: Continue data and password protection even if the database itself is compromised, known as “post-compromise security”
- Zero trust key management system: Virgil Security does not use a single master key for all customer operations or save old master keys
How is this different from TDE encryption?
- PureKit can distribute keys on a per-user basis
- PureKit allows for in-place key rotation, to avoid having to re-encrypt the entire database after key rotation
- Post-compromise security: the protected data will remain encrypted and useless after a database breach
- SQL Injection-Proof: PureKit is immune to SQL injections
What is post-compromise security
Post-compromise security (PCS) is the protection of data after the encryption key has been compromised. PCS can be provided by implementing the following features:
- Seamless key rotation:
- Keys can be rotated while the app is running
- Keys can be rotated both proactively or if there is a data breach
- Invalidation of stolen data
- Data cannot be decrypted without the cooperation of the crypto server, rendering any stolen data in a database useless
- Zero-Knowledge proof
- Crypto service proves all operations were performed using its private key
- Withstands both online and offline attacks
- Strict rate limiting per-user
- Need the private keys of both the application and the crypto service to make a password attempt.
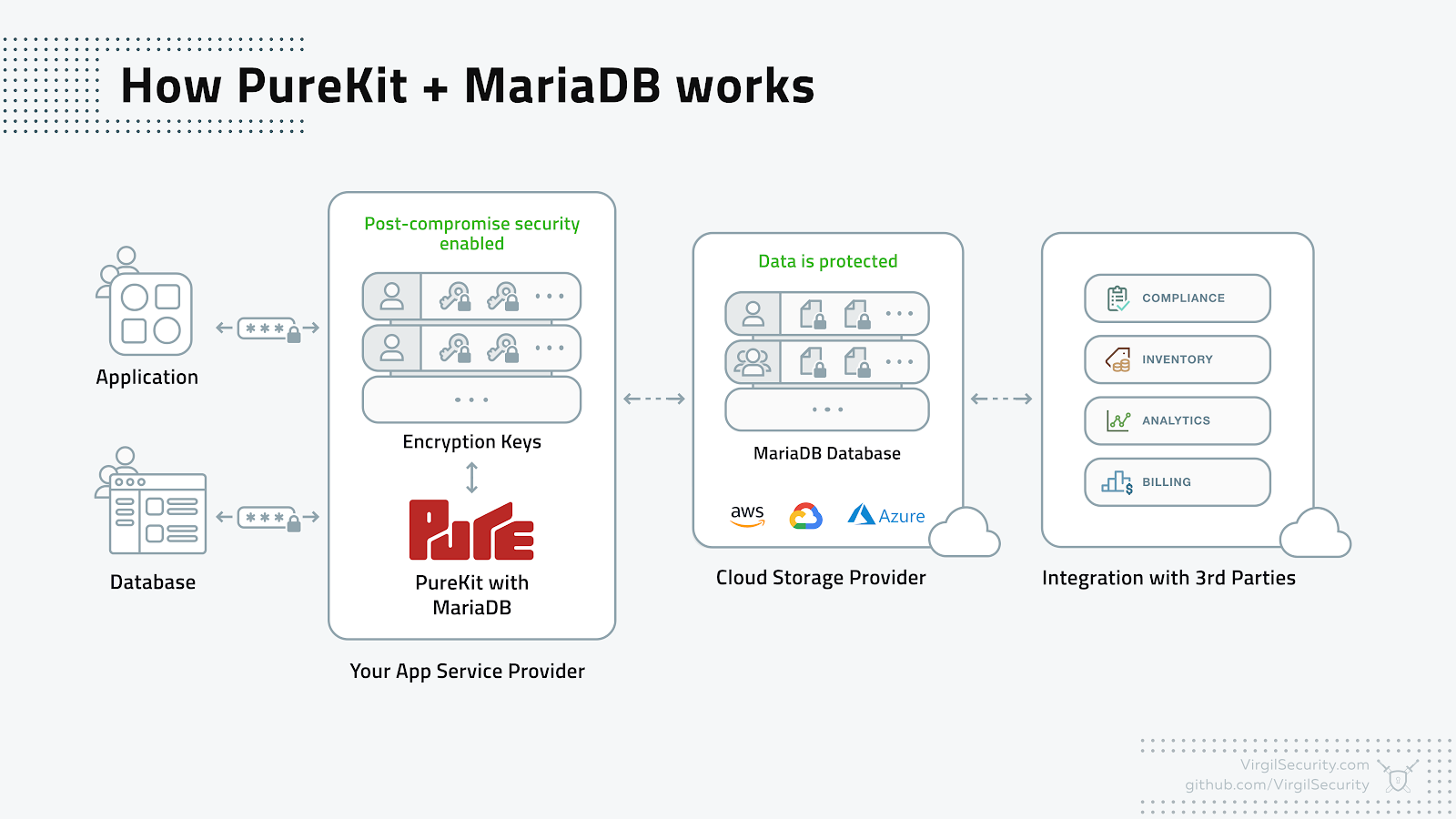
Virgil’s PureKit MariaDB demo
To set up and run the demo follow the README instructions
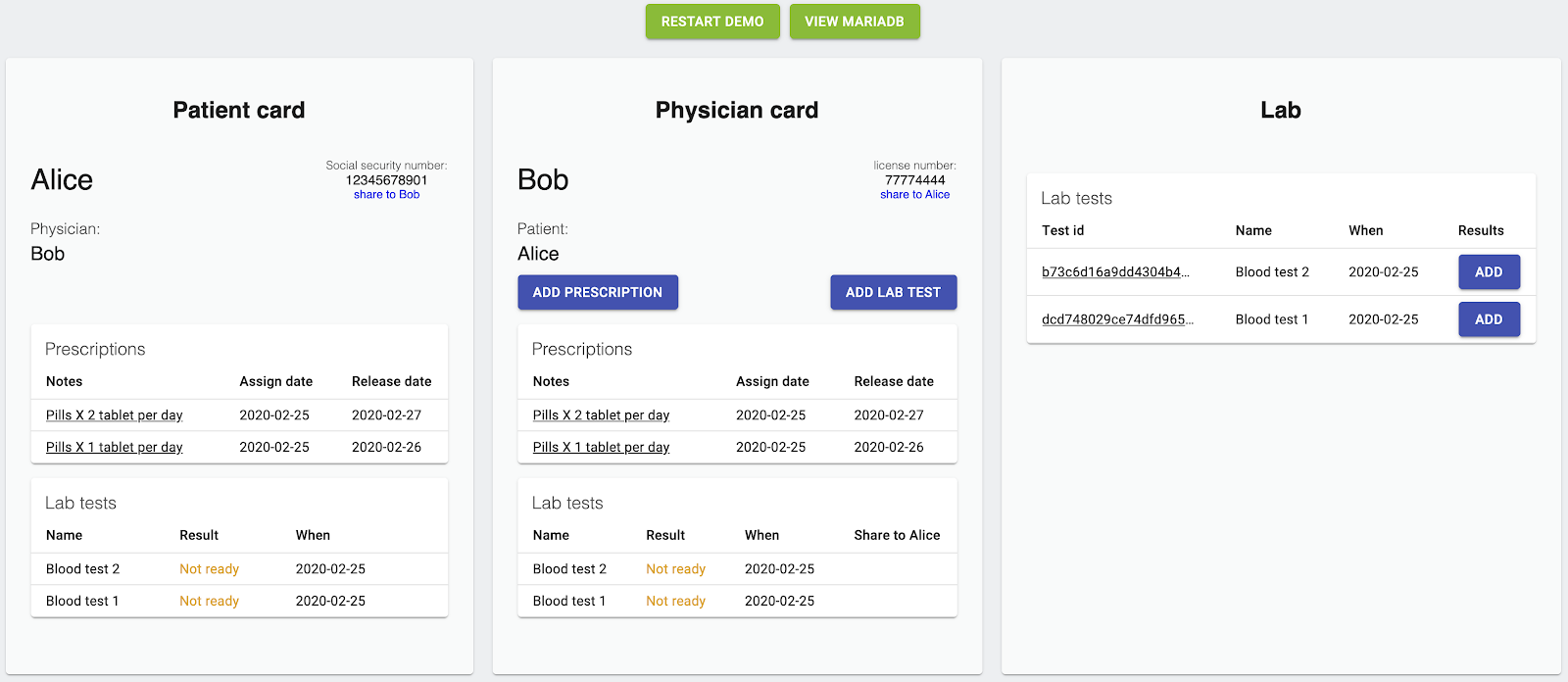
The MariaDB PureKit demo uses a hypothetical business scenario involving a patient, physician and laboratory, and shows how distinct roles within a customer’s application can be defined and used to restrict data access in a sensitive environment. When using the demo, you can see the results of your actions (e.g. the encryption methods) in the MariaDB database. Learn more here.
Learn More
Get started today with our PureKit developer guides at https://developer.virgilsecurity.com/docs/purekit.
Questions? Email support@VirgilSecurity.com or join our Slack community.
Virgil Security, Inc. makes every software developer a cryptographic expert. With Virgil Security, every developer can build encryption and verification into their products with no cryptographic training. Virgil’s open-source libraries are available for desktop, embedded (IoT), mobile, cloud, and web applications in a variety of modern programming languages. Founded in 2014, Virgil Security is headquartered in Manassas, Virginia. To learn more, visit https://VirgilSecurity.com/.