Category Archives: Foundation
In a movie theater near you, expect to soon see an explanation of MariaDB Server and MariaDB Foundation in your own language! That is, providing you speak one of the good dozen of languages we have frequently encountered in the MariaDB Server ecosystem.
English is a least common denominator
Like a majority of the MariaDB Server users, most of the developers behind MariaDB Server are non-native English speakers. We use Bad English as our lingua franca. Our pronunciation may be bearable to OK, but as with most techies, our understanding of written and spoken English is OK to good.
…
In this blog we are going to learn how to migrate data from Oracle to MariaDB.
To begin, we’ll learn the basics about Oracle database to have an understanding about the steps that are done on the demo example. After, we will create a table in Oracle and migrate it to MariaDB.
To migrate data from Oracle there are 2 ways:
- Dump Oracle data to CSV and load data in MariaDB.
- Use the Connect Storage Engine to create or insert into a table from Oracle’s source definition.
For demonstration, we are going to use a docker container with an Oracle Express Edition (XE) image.
…
When everybody and their grandmother are talking about ChatGPT, you know something is happening – something with significance outside the usual IT bubble. As the first in a series of blog entries, let me reflect upon what AI means for users of MariaDB Server – or, at least, what implications we at the MariaDB Foundation can see at this point in time.
The AI revolution is inevitable …
Pundits say that lawyers or programmers won’t be replaced by AI – but they will be replaced by lawyers or programmers that use AI. I would agree.
…
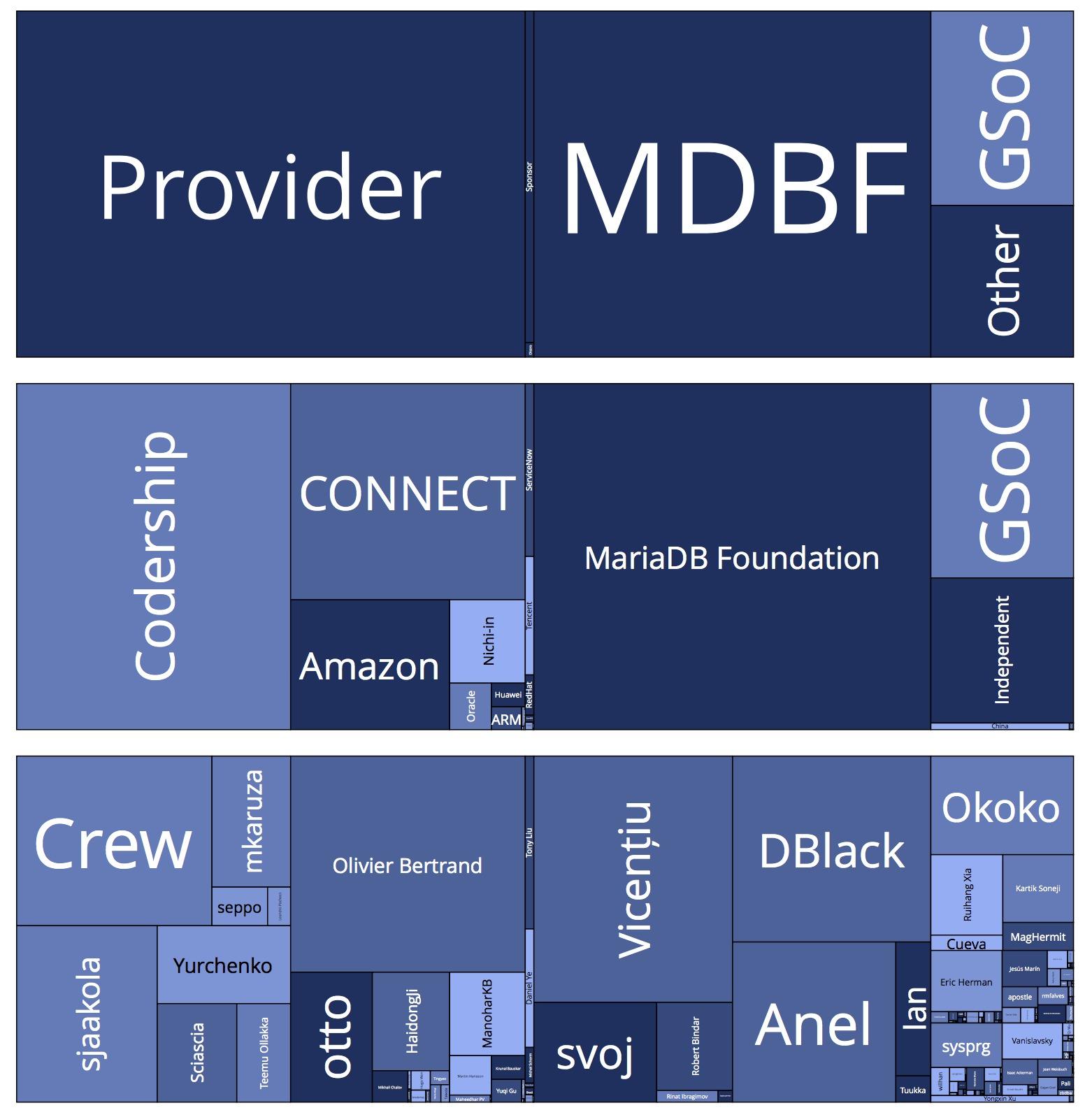
Due to a catalogue of issues our previous quarterly update for developer metrics was not published. This time, however, we have made quite a few changes. In this post, we will summarise 2022 and what has happened in the first couple of months of 2023. All the data for this blog post can be found in CSV format in the release section of the MariaDB Metrics repository, along with everything you need to generate the metrics yourself.
Changes to metrics gathering
For the main commit metrics, we use a tool called “GitDM” or Git Data Miner which was developed for the git kernel trees to group commits by people and organisations.
…
Continue reading “MariaDB Contribution Statistics, March 2023”
I’ve mentioned in past blog posts that not every contribution is a code contribution. There are many possible contributions that are valuable, including testing, bug reports, helping the community, etc.
Non-code contributions are quite invisible
Unfortunately, non-code contributions are sometimes invisible to the wider community, so today I wanted to shine a light on some such contributions. In this case, contributions made by one of our sponsors, Intel.
Intel is open source friendly
Intel have been an open source friendly company for a long time. But have recently pushed harder than ever towards open source, even giving their first ever new Innovation Award to Linus Torvalds.
…
Today, MariaDB Corporation announced that it completed its merger, landing on NYSE as “MRDB”. With MariaDB Corporation being our founding member as well as our primary code contributor, we want to congratulate what is now MariaDB plc for this remarkable achievement.
Joint goals
MariaDB Foundation and MariaDB Corporation, while independent entities, share a joint interest in the development and adoption of MariaDB Server. In the new scenario with what is now to be referred to as MariaDB plc being a publicly traded company, we expect further interest in MariaDB Server by the ecosystem and community.
…
In the last meeting, the MariaDB Foundation Board proposed the regular publishing of contribution statistics. This post is an update on our progress and the first report.
(more…) …
Something that is very important to us in the MariaDB Foundation is “Openness”. This is not only in the open source nature of MariaDB, but we are also very transparent in what happens with the MariaDB source code. With that in mind we have been working on ways to generate metrics that show information about the community in a consumable form.
(more…) …